Software development security is paramount today when cyber threats are rising. As software applications become more complex, they become more vulnerable to attacks. Security risks such as data breaches, identity theft, and cyber-attacks can have catastrophic consequences for businesses and individuals. Therefore, developers must implement robust security measures to mitigate these risks during software development. It includes secure coding practices, regular security testing, and implementing security protocols such as encryption, access control, and firewalls. By prioritizing software development security, businesses can protect their assets, safeguard customer data, and maintain their reputation in the market.
What are Security Risk in Software Development?
Security Risk in Software Development
Security risks are a significant concern in software development. Attackers can exploit vulnerabilities in software to gain unauthorized access, steal sensitive data, or cause damage to systems. Developers must prioritize security throughout the software development lifecycle, including conducting regular security audits and implementing secure coding practices. Failure to address security risks can result in severe consequences for individuals and organizations.
1. Software Systems That Are Not Being Maintained Regularly
It is crucial to maintain software systems regularly in software development. Failure to do so can lead to security risks that can compromise the entire system. Regular maintenance ensures that any bugs or vulnerabilities are identified and addressed promptly, reducing the risk of a security breach. Therefore, software development teams must prioritize regular maintenance to ensure the safety and security of their systems.

2. Poorly Written Code
Poorly written code can pose serious security threats in software development. Attackers can easily exploit vulnerabilities such as buffer overflows, SQL injection, and cross-site scripting if the code is incorrectly written and tested. Ensuring that code is developed securely and adheres to industry best practices can help prevent security breaches and protect users’ sensitive information.
3. Vulnerable Web Services
Vulnerable web services can pose a significant security risk in software development. To mitigate this risk, following software development security best practices, such as conducting regular security audits, implementing secure coding standards, keeping software up-to-date with patches and updates, and educating developers on secure coding practices, is essential. By adopting these practices, developers can help ensure their software is secure and protected against threats.
4. Insecure Password Management
Insecure password management is a significant security risk that software developers must be aware of. Hackers can easily access passwords if passwords are not stored securely, leading to data breaches and other cybersecurity threats. As such, it is essential to implement proper security measures and password management protocols to ensure that user data remains protected.
5. Outdated Software
Regarding software development, outdated software can pose a severe security risk. That’s why it’s essential to regularly update your software development tools to ensure they’re secure and up-to-date. A software development security checklist is one way to stay on top of this. It can help you identify potential vulnerabilities and take steps to address them before they become a problem. By prioritizing security in your software development process, you can help protect your users and businesses from harm.
Software Development Security Best Practices
Software Development Security Best Practices are crucial for protecting software against cyber threats. These practices include secure coding, continuous security testing, access control, and data encryption.
1. Make Software Security A Top Priority From The Beginning
Making software security a top priority is a critical software development security best practice. It involves implementing security measures throughout the entire software development life cycle, from design to deployment, to ensure that vulnerabilities are minimized, and user data is protected.
2. Provide Training On Security Awareness
One of the essential aspects of secure software development is maintaining security awareness among developers. Providing training on software development security best practices can help developers understand the significance of secure coding and testing. Developers can build robust and secure applications that protect users’ sensitive data by incorporating secure coding principles and practices into the software development lifecycle.
3. Utilize Code Reviews To Spot Possible Security Risks
One of the best practices in Software Development Security is to utilize code reviews to spot possible security risks. This process involves a thorough review of the code by other developers to identify any vulnerability and ensure the code is secure.
4. Utilize Tools For Static Code Analysis
Regarding software development security best practices, utilizing tools for static code analysis is crucial to minimize security risks. By scanning the code for potential vulnerabilities before deployment, developers can mitigate security risks and ensure a more secure software product.
5. Utilize Well-Known And Trusted Frameworks And Libraries
One of the best software development security practices is to utilize well-known and trusted frameworks and libraries. It helps to ensure that the software being developed is secure and reliable. By using established frameworks and libraries, developers can benefit from the collective knowledge and experience of the community.
6. Security Coding Standards And Recommendations
Security coding standards and recommendations are among the most critical software development security best practices. These standards help developers write secure code and reduce the risk of vulnerabilities and cyberattacks. Software organizations must adopt and enforce these standards to ensure the security of their products.
- The Use Of Encryption
Encryption is a critical security measure widely used in software development to protect sensitive information. It is considered a standard recommendation for securing data and preventing unauthorized access.
- Hashing Passwords
Hashing passwords is a crucial aspect of software development security. It is a commonly recommended practice to ensure data privacy and prevent unauthorized access. With hashing algorithms, passwords are converted into a unique set of characters that cannot be easily reversed or decrypted. It helps to ensure that even if a data breach occurs, user passwords are not easily compromised.
- Utilizing SQL Injection
SQL injection is a common vulnerability in software development that can compromise the security of a system. Developers must follow security coding standards and recommendations to prevent such attacks and protect their software from potential threats.
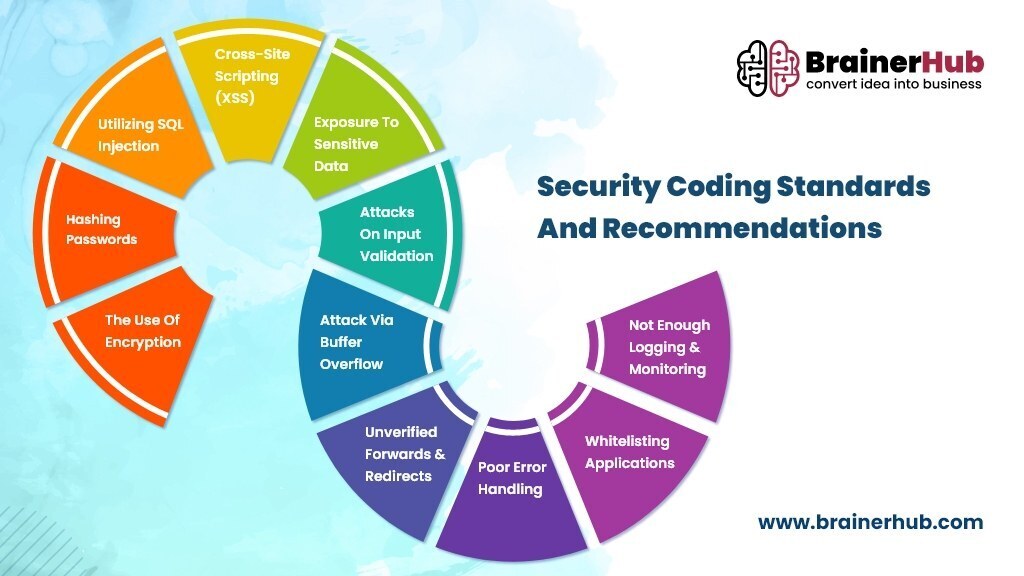
- Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a typical security vulnerability that can be prevented by following security coding standards and recommendations. Best practices include input validation, output encoding, and using security libraries and frameworks.
- Exposure To Sensitive Data
“Exposure to sensitive data” is crucial in security coding standards and recommendations. It involves limiting access to sensitive information and protecting it from unauthorized access or disclosure.
- Attacks On Input Validation
Input validation is an important security measure to prevent attacks such as SQL injection and cross-site scripting. Many coding standards and recommendations, such as OWASP Top 10, emphasize the importance of implementing strong input validation practices.
- Attack Via Buffer Overflow
Buffer overflow attacks are a common security threat that can be prevented by following secure coding practices during software development. Implementing input validation and memory allocation limits can help mitigate the risk of such attacks.
- Unverified Forwards & Redirects
Unverified forwards and redirects are common security vulnerabilities in software development. These occur when user input is not validated correctly, allowing attackers to redirect users to malicious websites or execute arbitrary code on the user’s device. It is essential to implement proper input validation to prevent these types of attacks.
- Poor Error Handling
Effective error handling is a critical aspect of software development security. Following coding standards and recommendations is essential to implement error handling correctly and securely. Please do so to ensure applications are protected from security threats.
- Whitelisting Applications
Allow listing applications is an important security measure recommended in software development. It involves creating a list of approved programs that can run on a system, which can help prevent unauthorized or malicious software from executing.
- Not Enough Logging & Monitoring
The lack of logging and monitoring is a typical security issue related to coding standards and recommendations. Implementing proper logging and monitoring mechanisms is essential to detect and respond to security incidents promptly.
7. Certification for ISO 27001
Companies need certification for ISO 27001 among the security coding standards and recommendations to ensure their software and systems are secure and protected against potential threats. This certification demonstrates a commitment to implementing and maintaining strong security measures and can give customers and partners’ confidence in the company’s ability to safeguard sensitive information. Achieving ISO 27001 certification involves rigorous testing and assessment of the company’s security practices, including code review, vulnerability testing, and risk management.
8. Examination of Penetrations
When it comes to ensuring the security of your code, it’s essential to consider all aspects of the development process. One key area to focus on is penetration testing. By examining potential vulnerabilities and testing them in a controlled environment, you can identify and address security risks before they become problematic. This practice is often included in security coding standards and recommendations to ensure a comprehensive approach to securing your code.
9. Adapt Safe Software Development Procedures To Your DevOps workflow
Adapting safe software development procedures to your DevOps workflow is vital while considering security coding standards and recommendations. It ensures that your software is secure and reliable and helps to prevent security breaches or data leaks.
Software Development Security Checklist
Developing secure software is crucial to protect against cyber-attacks. A security checklist ensures security is baked into the software development process. Key areas to consider include authentication, encryption, input validation, error handling, and access control. A comprehensive security checklist can help reduce the risk of security breaches.
1. Using Threat Models For Software Security
Threat models are an essential tool for software security in software development. Incorporating them into a security checklist can help identify potential vulnerabilities and mitigate risks.
2. Safe Software Coding
Safe software coding is a crucial aspect of software development security. A security checklist is essential to ensure all vulnerabilities are addressed and the software is secure.
3. Code Evaluation
Code evaluation is an essential part of software development security. It helps to identify vulnerabilities and reduce the risk of security breaches. A thorough code evaluation should be included in any security checklist.
4. Regular Testing
Regular testing is an essential part of software development security. It helps detect vulnerabilities early on and ensures the system is secure and reliable.
5. Securely Managing Configurations
To ensure software development security, it’s essential to manage configurations securely. A checklist includes version control, access limitation, encryption, secure communication, and regular review and updates.
6. Authorized Access Control
Ensure authorized access control measures are implemented in the software development by following the relevant security checklist.
7. Updates And Patches Regularly
One essential item on the software development security checklist is to ensure updates and patches are implemented regularly to maintain the security of the software.
8. Reaction To An Incident
When an incident occurs in software development, it is essential to have a response plan in place. It should include steps for containment, investigation, resolution, and communication.
9. Continuous Monitoring
Continuous Monitoring is an essential aspect of the software development security checklist. It involves regularly checking and analyzing system activity to detect threats and vulnerabilities and ensure the security of the software.
Conclusion
In conclusion, software development security must be integral to the software development lifecycle. Secure software development practices can help organizations prevent security breaches, data theft, and other cyber-attacks. Organizations can ensure that their software is built on a secure foundation by implementing security controls throughout the software development process. Software developers must stay updated with the latest security threats and vulnerabilities to provide their users with a secure and safe software product.